Table of Contents
Companies migrate to the cloud to take advantage of its flexibility and pay-as-you-go model, which can save costs. However, in most cases, performing the migration in one go is unrealistic.
Why? Legacy monolithic applications are usually one reason, as their complexity makes them difficult to migrate. You might think a "lift and shift" approach, simply migrating all servers to the cloud, is an option. It might seem feasible, but it doesn't provide the full benefits of cloud computing. This approach prevents you from taking advantage of the flexibility or using modern architectures like microservices or serverless functions, which can give you a competitive advantage.
Instead, I see it as a collaborative journey where the Solutions Architect works with the customer to achieve their goals.
Migrations typically take time and are done in batches. This is where this post becomes relevant, as it focuses on the need for connectivity from on-premises environments to cloud providers like AWS, GCP, Azure, or others. Even multi-cloud connections are possible.
Spoiler! In this post, I'll focus on AWS as a cloud provider.
Even some customers might need this connectivity temporarily, while others may require it permanently. Therefore, a customer's decision depends on their specific needs: whether they want to fully migrate to the cloud or continue using some on-premises servers in combination with the cloud.
Which AWS VPN solution to choose?
In AWS, there are a few ways to achieve this. Let's take a look at them!
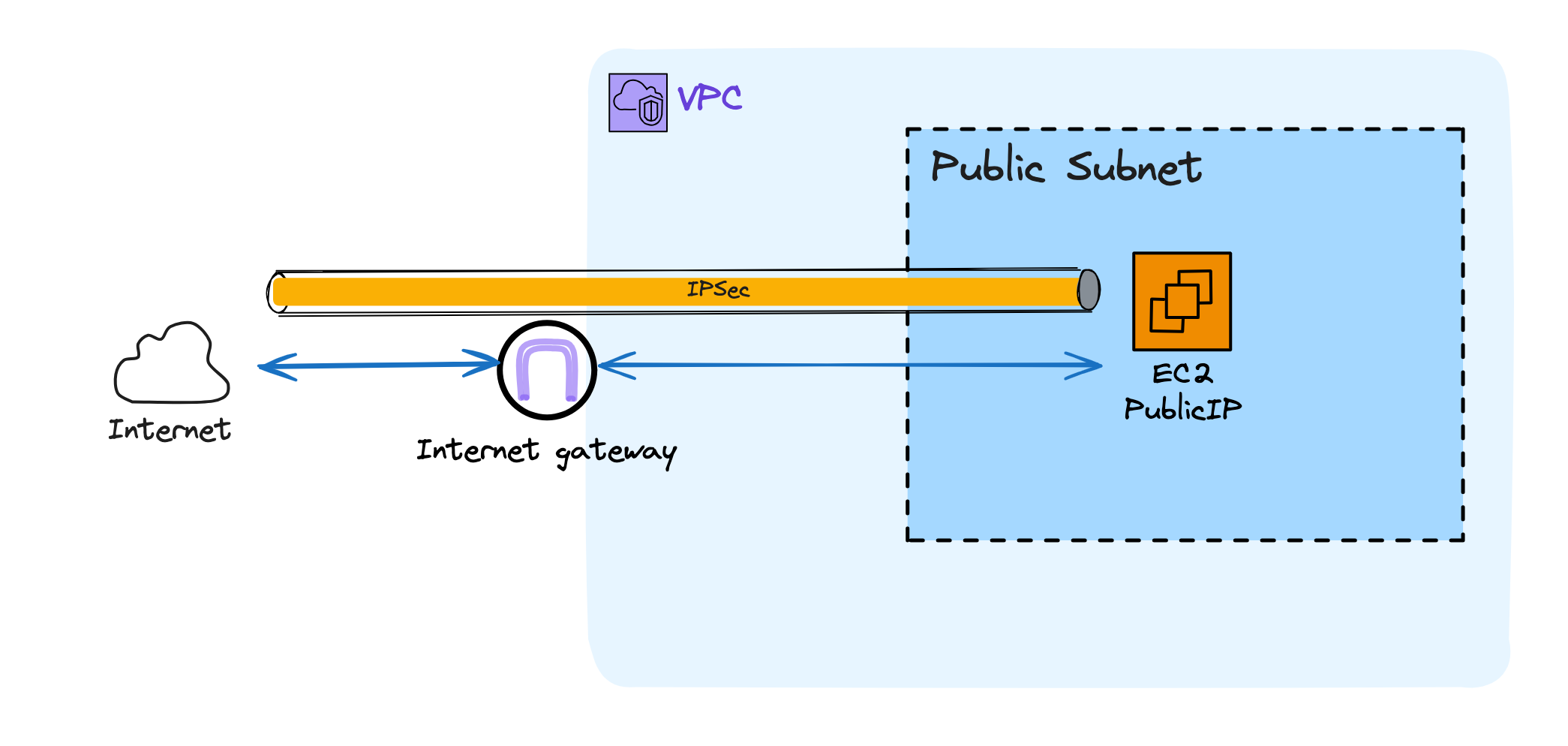
Secure Your AWS VPC: Third-Party VPN via Internet Gateway
This solution offers one of the most cost-effective ways to establish a VPN connection to your VPC. The reason for this is because you are responsible for maintaining the resources and their software.
In this solution, we'll start with a design that uses a public subnet within the VPC to host an EC2 instance. While I'm not going to start with a redundancy and high-availability networking design, it's something you should consider for your solutions. In case you choose to implement that.
To secure access to the VPC, you'll need to install a third-party VPN software, like OpenVPN, on the EC2 instance. Of course, this software needs to be maintained by you, including dealing with all the patches, issues, and whatever else happens.
Once the VPN software is installed and internet connectivity is provided to the instance, customers can create an IPSec tunnel from their on-premises network or even from another cloud provider to AWS.
PROS
- Cheap solution
- Completely customised, you control everything
CONS
-
AWS doesn't fully manage this. You'll need someone to manage both the EC2 instance and the separate VPN software.
-
To ensure redundancy, you'll need to add a load balancer and an auto-scaling group to your design. This will distribute the instances across different Availability Zones (AZs).
-
VPN tunnels are established over the internet. The quality of your connection depends on the internet service provider's (ISP's) network. There's no guarantee that the connection will not have congestion, nor that the path between both destinations is the one with the least latency. A solution for that is to use Global Accelerator as an endpoint (like EC2 instances, Elastic IP Address, Network Load Balancer, or Application Load Balancer). In this way, you ensure that customer traffic reaches the closest AWS accelerator endpoint.
Costs to consider
- EC2 incurs a cost per hour while you are using it and per outbound traffic.
- There is no cost associated with the Internet Gateway (IGW).
AWS Site-to-Site VPN: Secure Cloud Connectivity
If you want to have peace of mind by not having to patch your EC2 instances, VPN software, nor design a highly available and redundant solution, then you should go for the option of an AWS fully managed system called AWS VPN Site-to-Site.
Easy to configure with a few clicks on the console. Or, if you're more adventurous, you can use the CLI or infrastructure automation tools like CDK. We'll skip a deep dive into this topic for now.
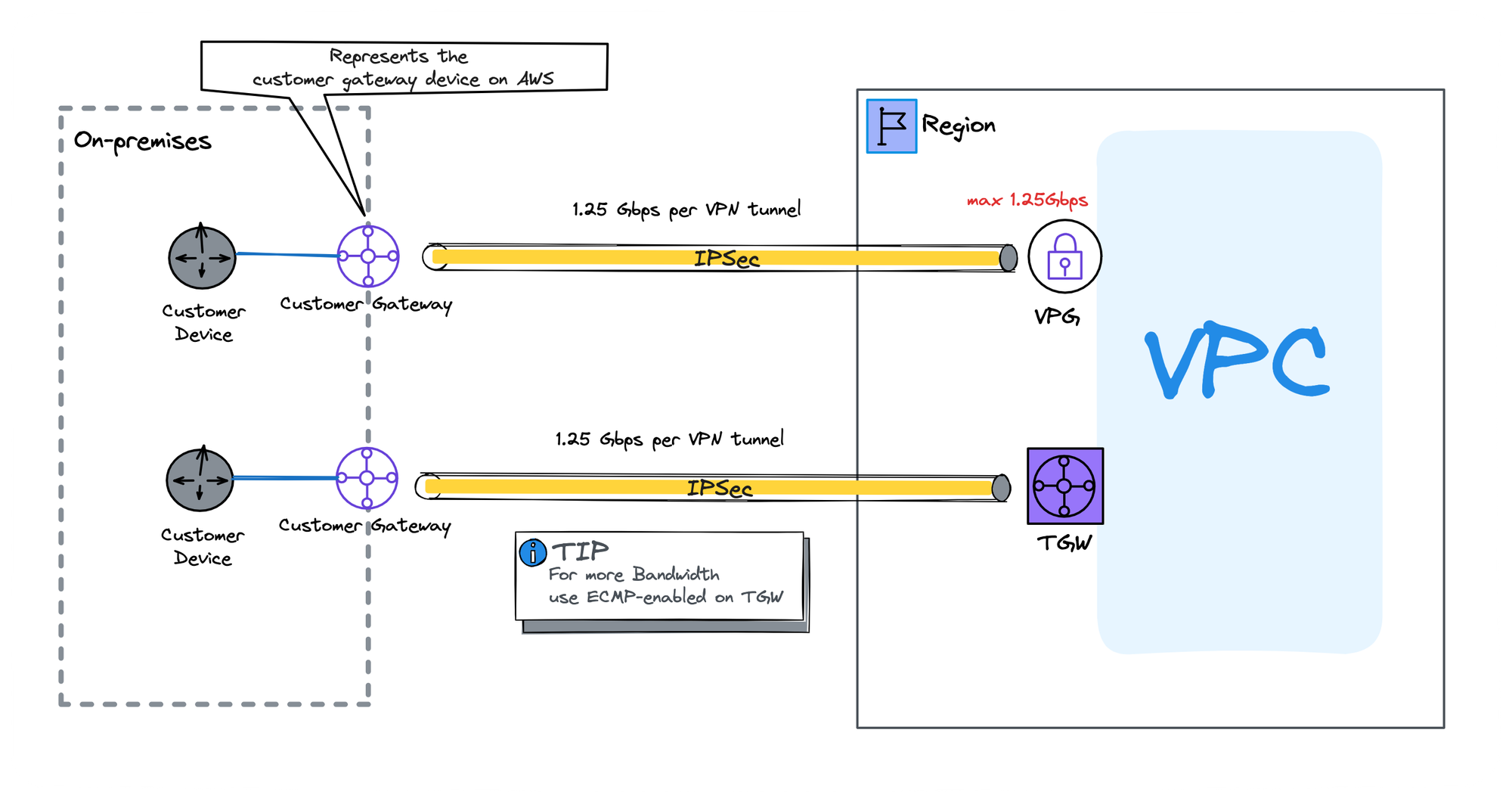
Components of the AWS VPN Solution
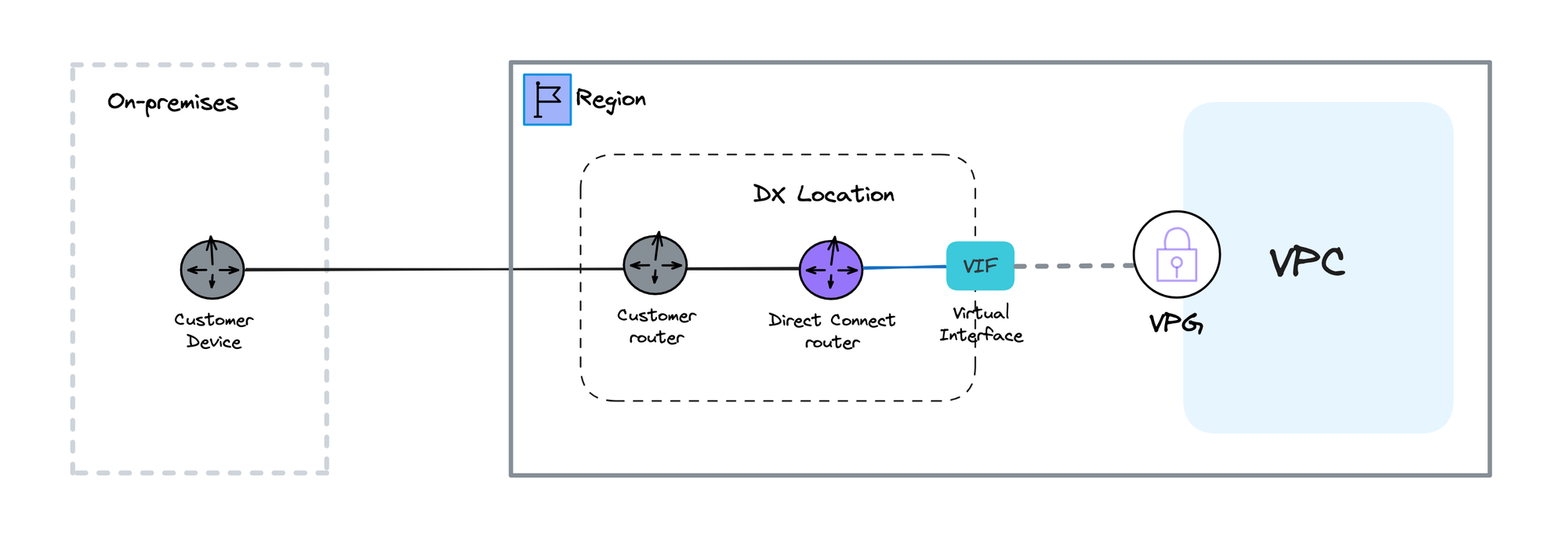
- Customer device: A physical device located on the customer's premises.
- Customer Gateway: Represents the customer gateway device in AWS.
- VPN tunnels: IPsec tunnel connections that secure and encapsulate all the traffic between the customer and AWS.
- VPG (Virtual Private Gateway): A cloud gateway that creates a secure, encrypted tunnel between on-premises networks and the AWS VPC.
- TGW (Transit Gateway): A central router that allows you to connect multiple attachments, including VPCs and other TGWs.
Where to terminate your on-premises VPN connections on AWS.
On AWS, there are two options for terminating your VPN connections: Virtual Private Gateway (VPG) and Transit Gateway (TGW). The choice, as always, will depend on your or your customer's needs. We'll delve deeper into both options in the coming sections.
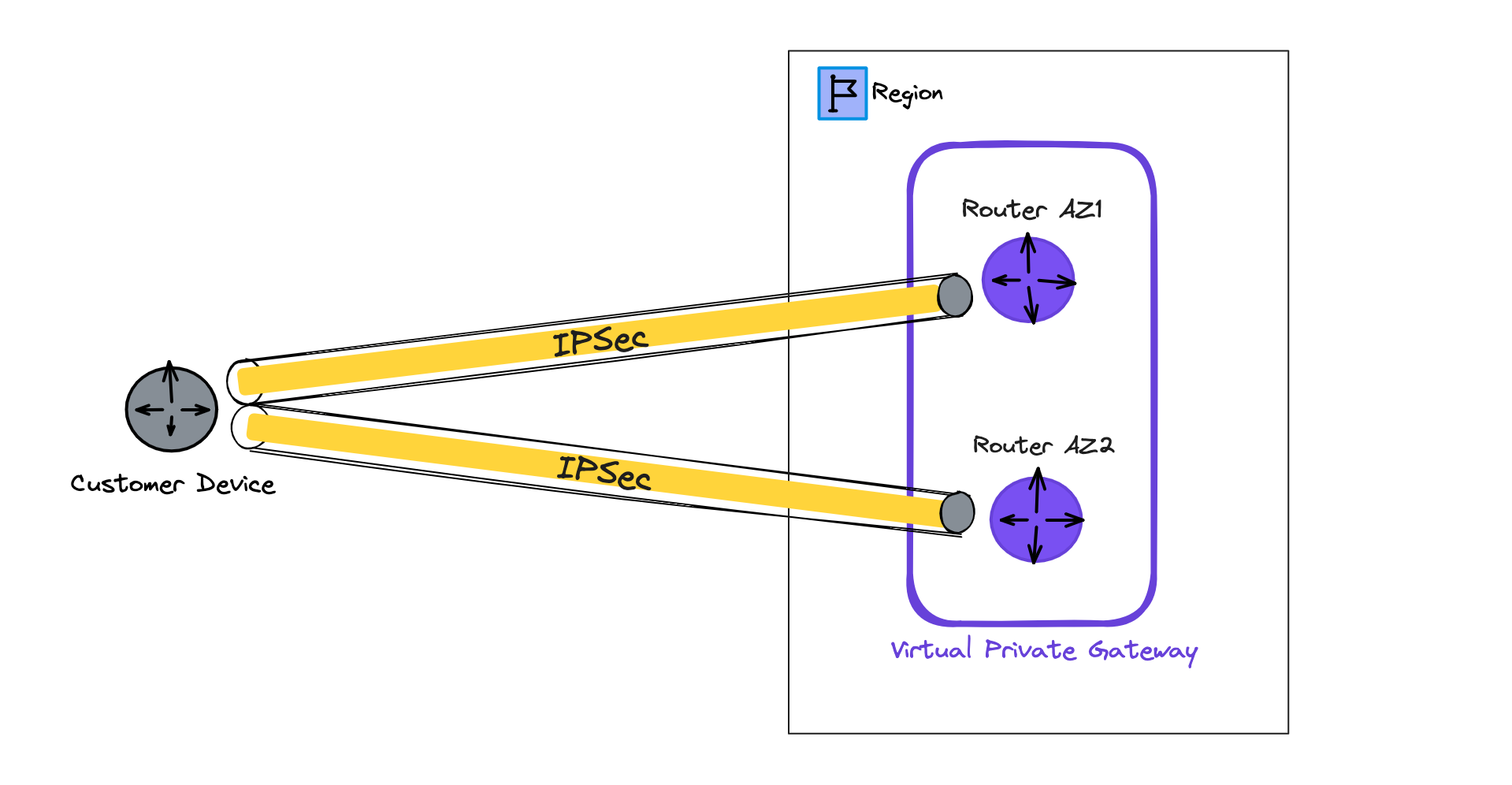
Understanding AWS VPN redundancy
AWS VPN connections offer built-in redundancy to ensure reliable connectivity between your on-premises network and your VPC.
Here's how it works:
- Dual VPN Tunnels: Each VPN connection establishes two separate tunnels. These tunnels act as independent paths for data transmission, enhancing reliability.
- Physical diversity: Each tunnel terminates on an Elastic Network Interface (ENI) in a different Availability Zone (AZ) within the same region. This ensures that a failure in one AZ won't disrupt the entire connection.
- Customer Gateway: The VPN connection itself associates with a customer gateway device located on your on-premises network.
AWS Virtual Private Gateway Site-to-Site VPN Connections: Secure Cloud Connectivity Explained
Let's consider the option of using a Virtual Private Gateway (VPG).
While both VPN tunnels are established to the VPG, traffic cannot be routed over both simultaneously. In networking terminology, this is because VPGs do not support Equal Cost Multipath (ECMP). This limitation stems from the VPG's design, which allows it to only send traffic over one active tunnel at a time. The primary tunnel is selected based on factors like the Multi-Exit Discriminator (MED) value.
ECMP is NOT supported by VPG 🙁.
Use case
A customer who wants to connect their on-premises network to the AWS cloud is looking for a simple cloud configuration with a single VPC and expects low traffic volume, under 1.25 Gbps.
Virtual Private Gateway Limitations
Let's explore the most important limitations of a VPG VPN connection. you can find a complete list in the AWS documentation AWS Site-to-Site VPN quotas.
- Each tunnel is limited to 1.25 Gbps of traffic. While there are two tunnels for redundancy, only one can transmit or receive customer traffic at a time. This effectively limits the overall throughput of a Virtual Private Gateway to 1.25 Gbps, the capacity of a single VPN link.
- A VPC can only have one attached VPG. This is less than ideal for scenarios requiring more capacity, as adding another VPG necessitates creating a new VPC and establishing peering between them. Peering multiple VPCs together can create scalability challenges.
For scaling VPN site-to-site connections, a simpler and cleaner solution is to leverage Transit Gateway (TGW). You can terminate all VPN connections on the TGW and attach all VPCs to it.
We'll discuss using a Transit Gateway (TGW) in the next section.
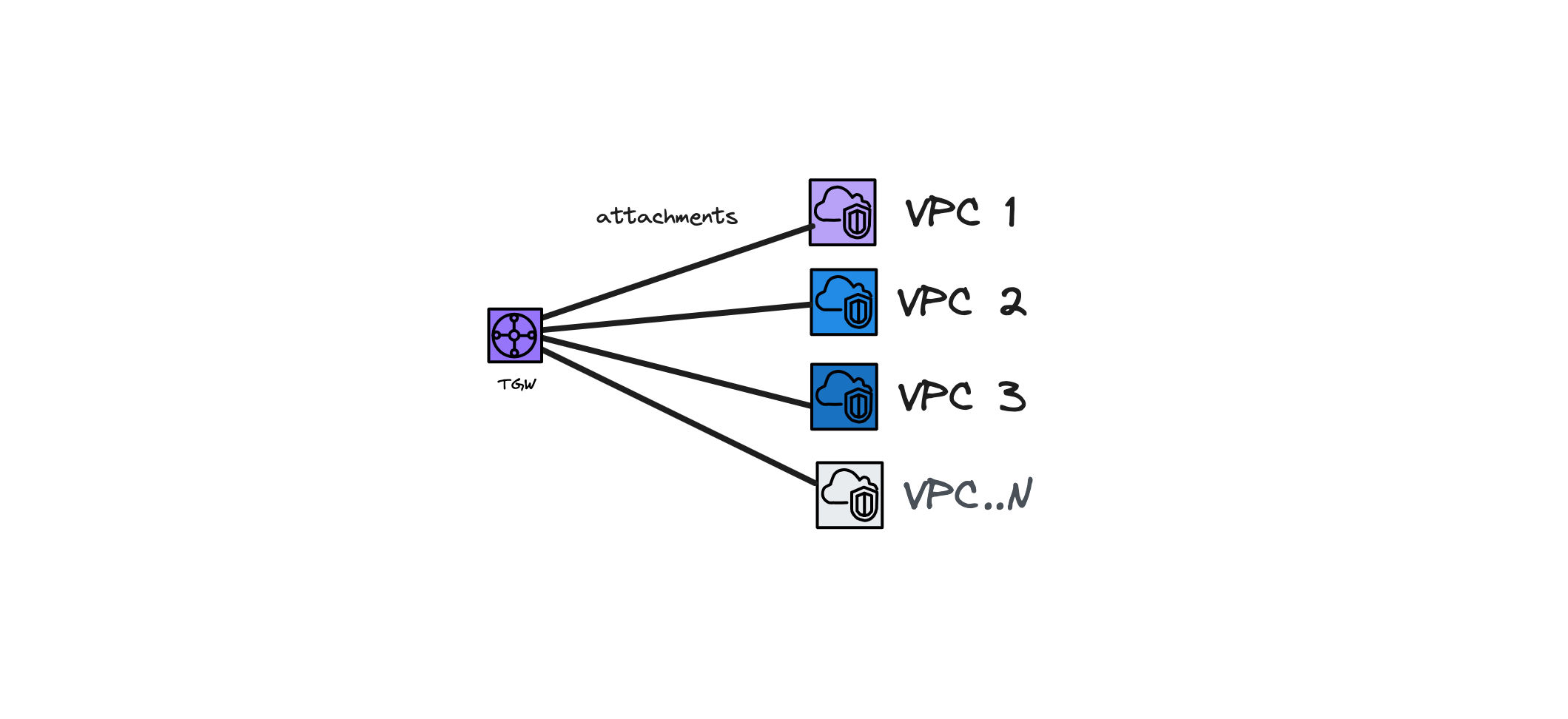
AWS Transit Gateway Site-to-Site VPN Connections: Simplifying Multi-VPC Networking
TGW is a regional service that offers high availability across multiple Availability Zones (AZs). AWS manages all infrastructure, so you can focus on the configuration.
By using TGW, you eliminate the need for individual VPN connections for each VPC. Instead, you can centrally configure and manage all Site-to-Site VPN connections through a single TGW route table. This simplifies management and operational tasks.
Use case
There are 2 scenarios that you should consider using TGW.
First, multiple remote sites on-premises and office locations. Image having multiple offices that need access to AWS.
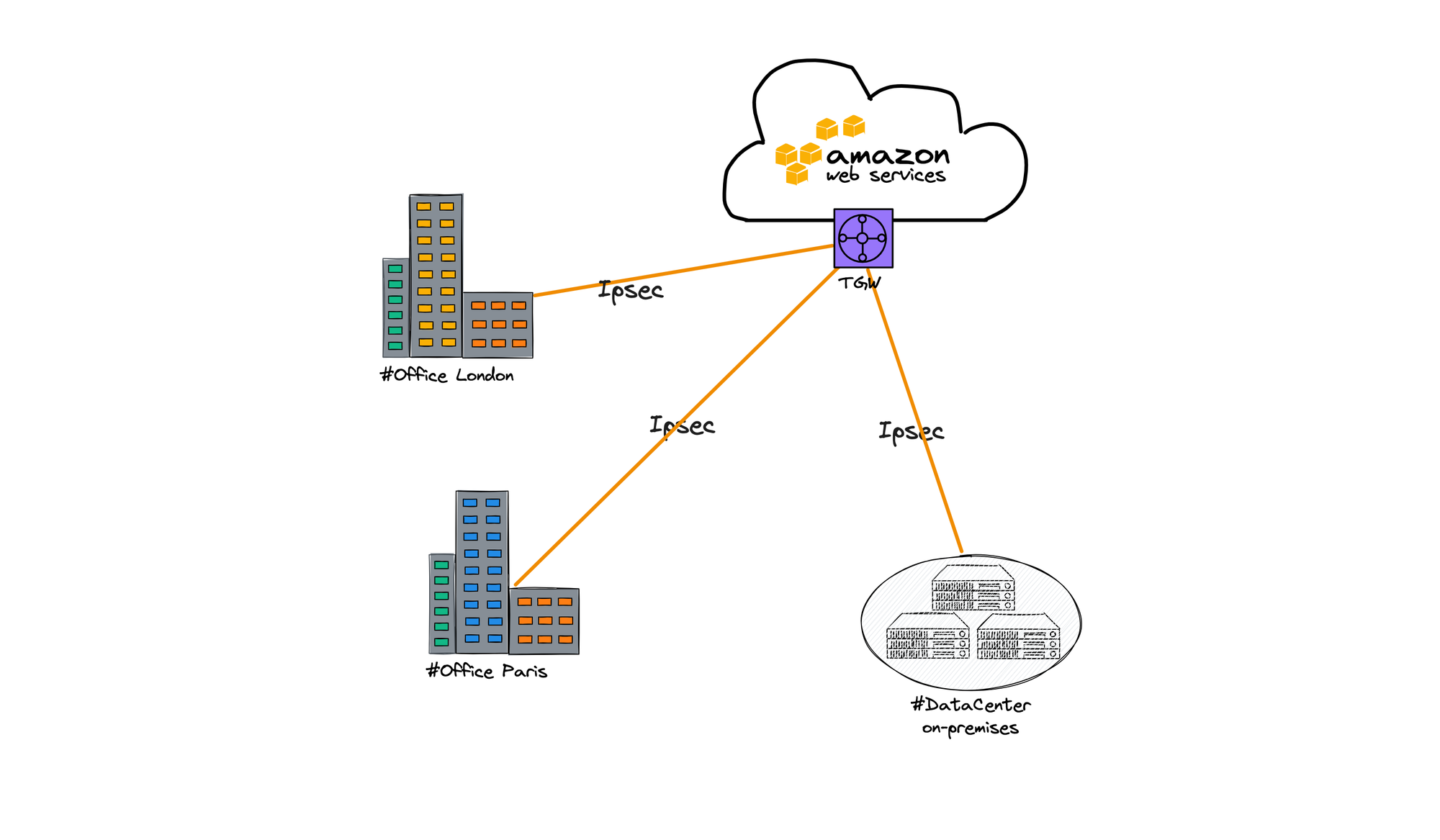
Second, we’ll focus on the AWS side, having a big number of VPCs. TGW is regionalised, so all the VPCs need to be in the same region. In case you need to connect data between regions you’ll have to peer between TGWs.
Things to consider
- This solution is fully managed by AWS.
- No IGW needed to access the VPC.
Transit Gateway Limitations
Let's get to the most important limitations for a TGW VPN connection. You can check all of them in the AWS documentation (Transit Gateway Quotas)
- It inherits the individual VPN tunnel limitation of 1.25Gps. To achieve higher throughput, you'll need additional VPN connections to the TGW. Then, you can use ECMP (Equal Cost Multipath) to balance customer traffic across these multiple VPN connections.
- 50 VPN Site-to-Site connections per region. However, you can request a quota increase from AWS Support.
- 5,000 attachments, these can be VPC, VPN and TGW.
- up to 7,500,000 packets per second per transit gateway attachment.
Costs to consider
- Per VPN per hour
- Data transfer out
AWS Direct Connect: High-Performance Cloud Networking Solution
The third option for connecting your on-premises environment to your VPC is Direct Connect (DX). Unlike the previous options, which route traffic through the internet (potentially leading to unreliability), DX provides a dedicated connection.
This solution offers the most reliable and consistent performance with premium network connectivity, essentially acting as a dedicated bandwidth line between your on-premises environment and the AWS region. While it's not a literal cable connection (we'll discuss this in another post), it offers a similar level of directness.
To establish a Direct Connect connection, you'll typically need to work with your internet service provider (ISP) or an AWS Direct Connect partner that has a presence in the desired region. You can find a complete list of available locations at https://aws.amazon.com/directconnect/locations/.
Virtual Private Gateway (VGW) vs. Direct Connect Gateway (DGW)
The physical connection to the AWS region established, another factor to consider is VPC location. Are your VPCs in the same region or spread across multiple regions? This decision point influences your choice between a Virtual Private Gateway (VGW) and a Direct Connect Gateway (DGW).
If you're not sure about the future, choosing a DGW is a good idea. It can handle more growth and avoid problems later if you move your VPCs to different regions.
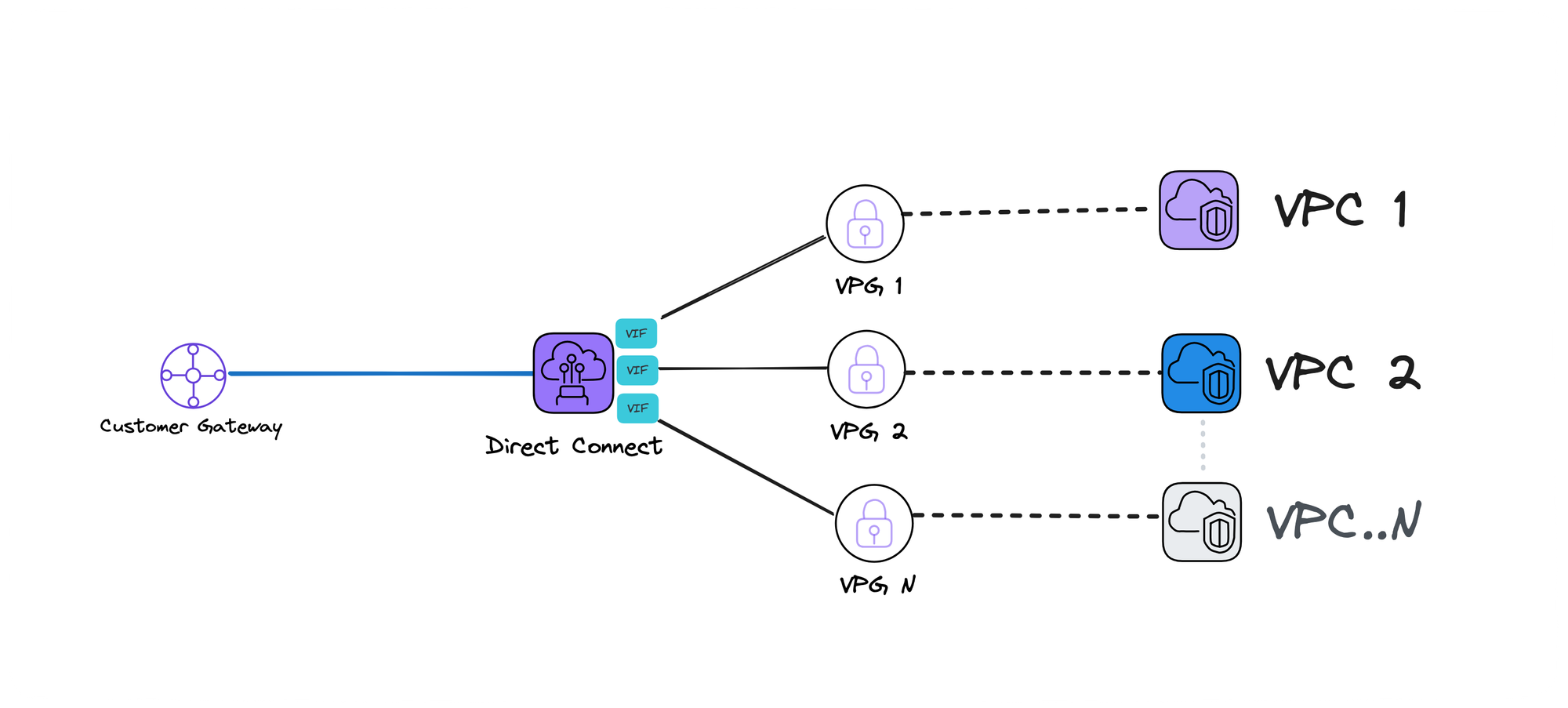
Same region VPCs
This solution is ideal if all your VPCs reside in the same region and you have no plans for multi-region expansion.
Remember! Each VPC can only have one VPG, necessitating a one-to-one mapping between them.
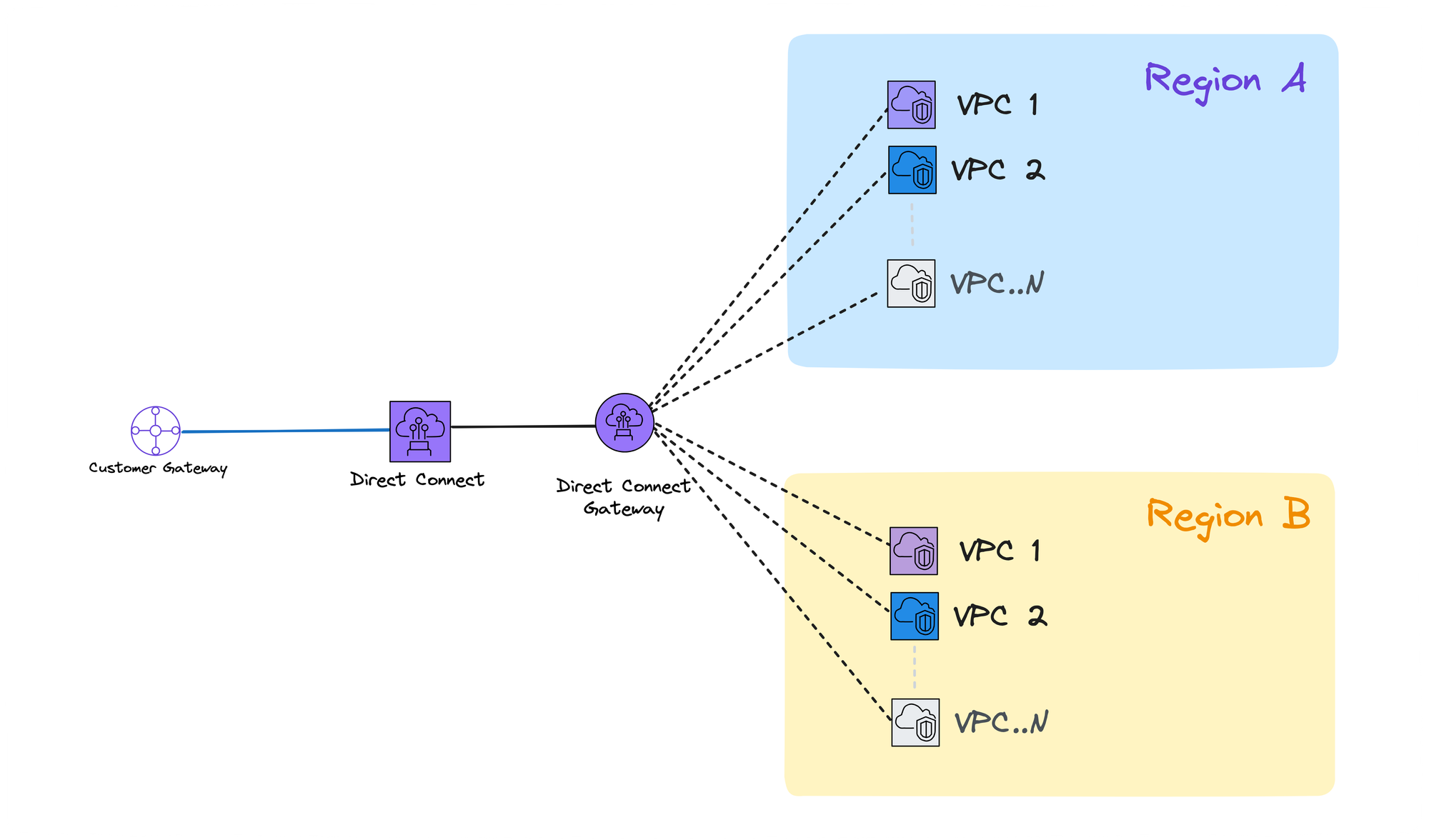
Multi-Region VPCs
This solution makes setting up Direct Connect and connecting it to your VPCs much easier. You simply need to create a Direct Connect Gateway (DGW) in your region. The advantage of a DGW is that it can connect to any VPC in any region. This makes things much simpler to design
Important Note: Direct Connect Gateway does not facilitate communication between VPCs. If inter-VPC communication is required, consider using VPC peering or Transit Gateway (TGW), which will be covered in the next section.
Transit Gateway (TGW) in Each Region
Another option, and maybe my favourite, is to use a Transit Gateway (TGW) in each region. A TGW acts like a central connection point for all your VPCs in that region, allowing them to talk to each other. The connection from your physical connection point goes through the Direct Connect Gateway to your VPCs.
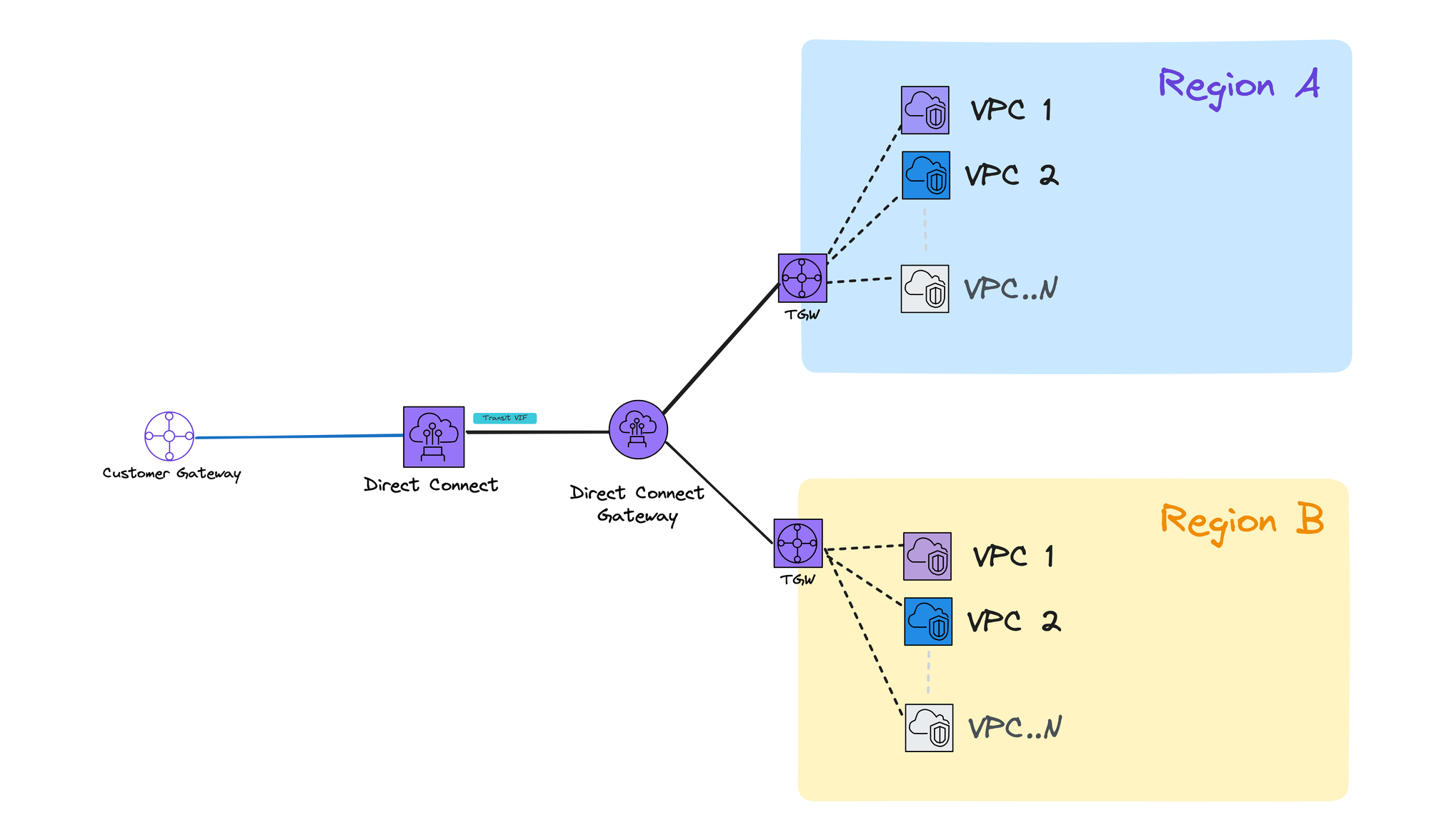
Use case
An AI startup is building a powerful LLM specifically designed for real-time customer service chatbots. To train this powerful LLM for real-time customer service chatbots, a startup specialising in AI requires massive amounts of text data.
Direct Connect Limitations
Let's get to the most important limitations for Direct Connect. You can check all of them in the AWS documentation.
Virtual Interface (VIF):
- 50 VIFs per Direct Connect connection (maximum 50 VPCs)
- VIF connections are limited to VPCs located in the same region
- 100 BGP routes for IPv4 and IPv6 per private or transit VIF
- Advertising more will make your BGP session go down
- 1,000 BGP routes for IPv4 and IPv6 per public VIF
Transit Gateway Limitations (if you’re using one):
- 20 VPC attachments per Direct Connect Gateway
- 5 Transit Gateway connections per Direct Connect Gateway
- 4 Transit VIF per dedicated connection
Costs to consider
- Per Direct Connection per hour
- Capacity of maxim network bandwidth that you can transfer
- Data transfer out
Pro TIP! Enhance Performance with AWS Global Accelerator
Use Global Accelerator to significantly improve the responsiveness and performance of your applications for your customers or on-premises users by routing traffic onto the AWS backbone as soon as possible.
Conclusion
Alright, let's wrap this up!
We've explored a range of AWS networking solutions, from budget-friendly options like Internet Gateway with third-party VPN to high-performance choices like Direct Connect. Remember, the best fit depends on your specific needs – whether that's cost, performance, or scalability.
Here's the bottom line:
- For quick or temporary setups, go with Internet Gateway and third-party VPN.
- For more permanent solutions, consider AWS VPN Site-to-Site (use VPG for single VPC, TGW for multi-VPC).
- If you need speed and performance, Direct Connect is your go-to.
Whatever you choose, keep security front and center, and be ready to adapt as your needs evolve.
Happy Cloud!
